Unstable testing environments: a headache for any quality team. Whether you're running manual or automated tests, a flaky environment blocks progress. This hands-on guide tackles AWS infrastructure testing head-on, exploring key services like CodeBuild and showing you how to build a robust CI/CD pipeline. We'll also look at how MuukTest can simplify your test automation infrastructure and boost your confidence in your AWS managed services.
The best way to solve this problem is to understand the software testing infrastructure and work closely with the DevOps team to build that infrastructure. The amalgamation of testing needs and DevOps gives rise to TestOps. This article outlines my experience with the different components within AWS that can help build a stable and reliable testing infrastructure for a successful CI/CD pipeline.
What Is TestOps?
Any kind of operations infrastructure required to set up a testing environment or for running test automation is referred to as TestOps. These days, some companies have dedicated personnel who address test operations challenges.
For the scope of this article, we will walk through the different components on AWS that play a role while setting up a CI/CD pipeline for running a simple application and running tests in a staging/QA environment to validate that the application loads as expected.
Different components of AWS that aid in building a CI/CD pipeline

Key Takeaways
- Reliable testing infrastructure is essential for smooth CI/CD pipelines. Leverage AWS services like CodeCommit, CodeBuild, CodePipeline, and CodeDeploy to create a robust and scalable testing environment.
- Testing directly in the cloud offers the most realistic results. Combine the speed of local testing tools like LocalStack with the accuracy of cloud-based testing in a non-production environment for a comprehensive testing strategy.
- Automate and streamline your testing for faster, more reliable deployments. Integrate automated tests into your CI/CD pipeline and use IaC tools like Terraform and AWS CDK. Explore AI-powered automation services like MuukTest to accelerate achieving complete test coverage.
AWS Code Commit
If your company hires full-time developers and contractors, how do you manage access to repositories for both groups?
AWS Infrastructure Testing: A Comprehensive Guide
Thoroughly testing your AWS infrastructure is key for a smooth-running application. It’s not just about checking if things work; it's about making sure your system can handle real-world conditions, performs efficiently, and stays secure. Let's break down why this matters and how to approach it effectively.
Why Test AWS Infrastructure?
Testing your AWS infrastructure is crucial for several reasons, the most important being to ensure reliability and performance. As many experts suggest, testing directly in the cloud using a non-production environment is best practice. This lets you validate your infrastructure in a setting that closely mirrors production, without the risks of a live environment. Think of it as a dress rehearsal before the big show.
Ensuring Reliability and Performance
To ensure reliability and performance, using local testing tools can be incredibly helpful. LocalStack, for example, provides local versions of many AWS services, which speeds up development and testing cycles. This allows you to conduct tests in a controlled environment, ensuring the infrastructure behaves as expected before deployment. Additionally, Infrastructure as Code (IaC) is essential. Tools like Terraform help manage and automate the creation and configuration of these test environments, ensuring consistency between testing and production.
Cost Optimization
Testing your AWS infrastructure also offers significant cost advantages. By conducting tests locally, you can avoid AWS charges and speed up the testing process. Local testing not only reduces costs but also makes the entire process more efficient, allowing teams to iterate and improve infrastructure more quickly. Early testing can catch potential issues that could become expensive problems down the line.
Security and Compliance
Security and compliance are paramount when deploying any infrastructure. Following least-privilege principles when deploying to AWS is essential. This means granting only necessary permissions, minimizing the risk of security breaches. Equally important is avoiding running LocalStack in privileged mode within CI/CD pipelines. This practice helps maintain a secure testing environment and protects your systems from potential vulnerabilities. A secure system is a reliable system, and incorporating robust testing practices from the start can contribute significantly to a secure and compliant infrastructure.
CodeCommit competes with Github by providing a fully-managed source control service that hosts git-based repositories. It eliminates the need to create your own repository or worry about scaling your infrastructure when your company’s needs grow. It stores source code and also works seamlessly with your existing Git tools. If your company already hosts its services on AWS, then it is easier to leverage CodeCommit while building your CI pipeline.
It is very secure as it automatically encrypts your files, even during a build. AWS integrates with Identity and Access Management (IAM) to customize user-specific access to repositories. For added security, CodeCommit also uses MFA. These customizations include user profiles that control who has access to which repositories at an organizational level.
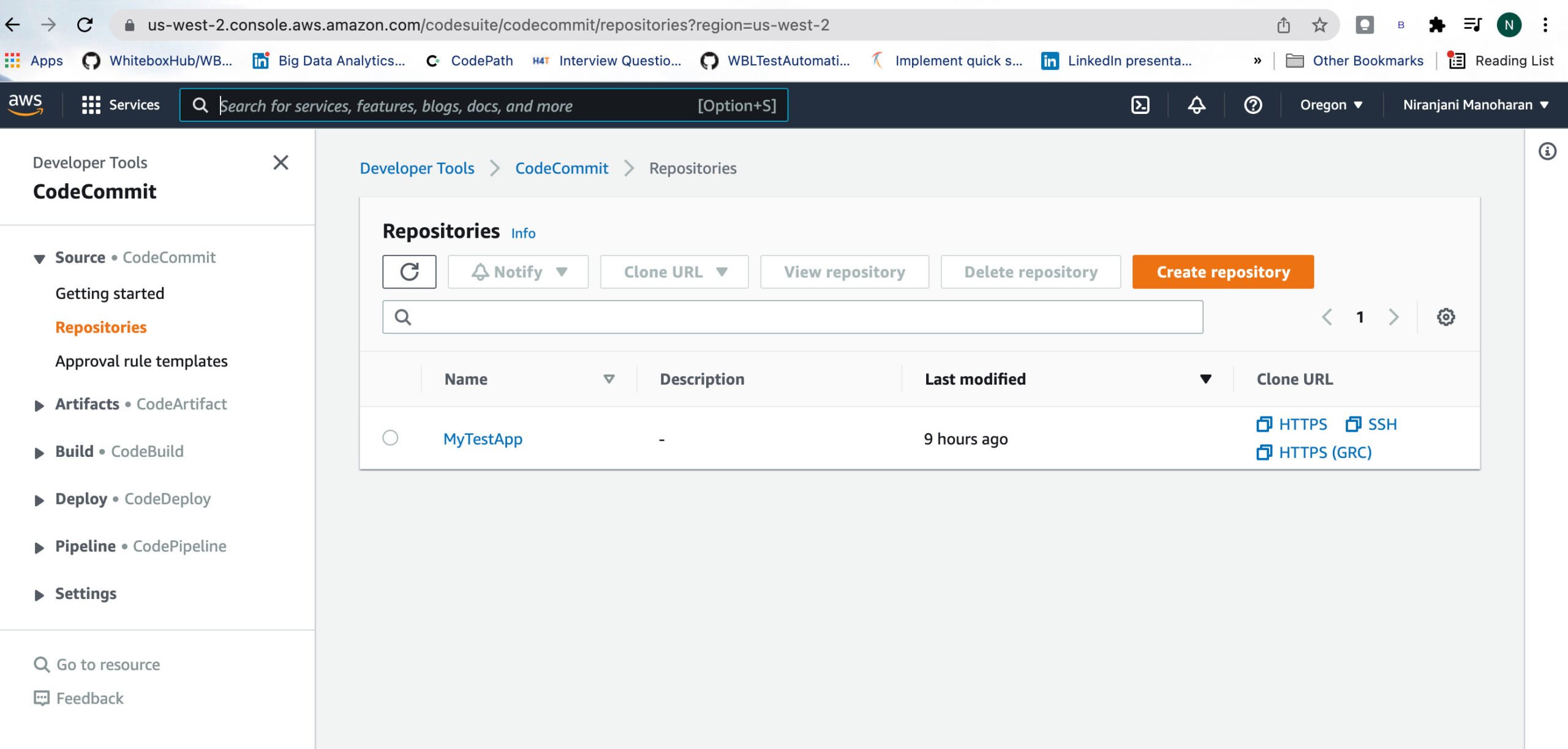
The above image shows my repository on my AWS management console. As you can see, the GUI is fairly user-friendly.
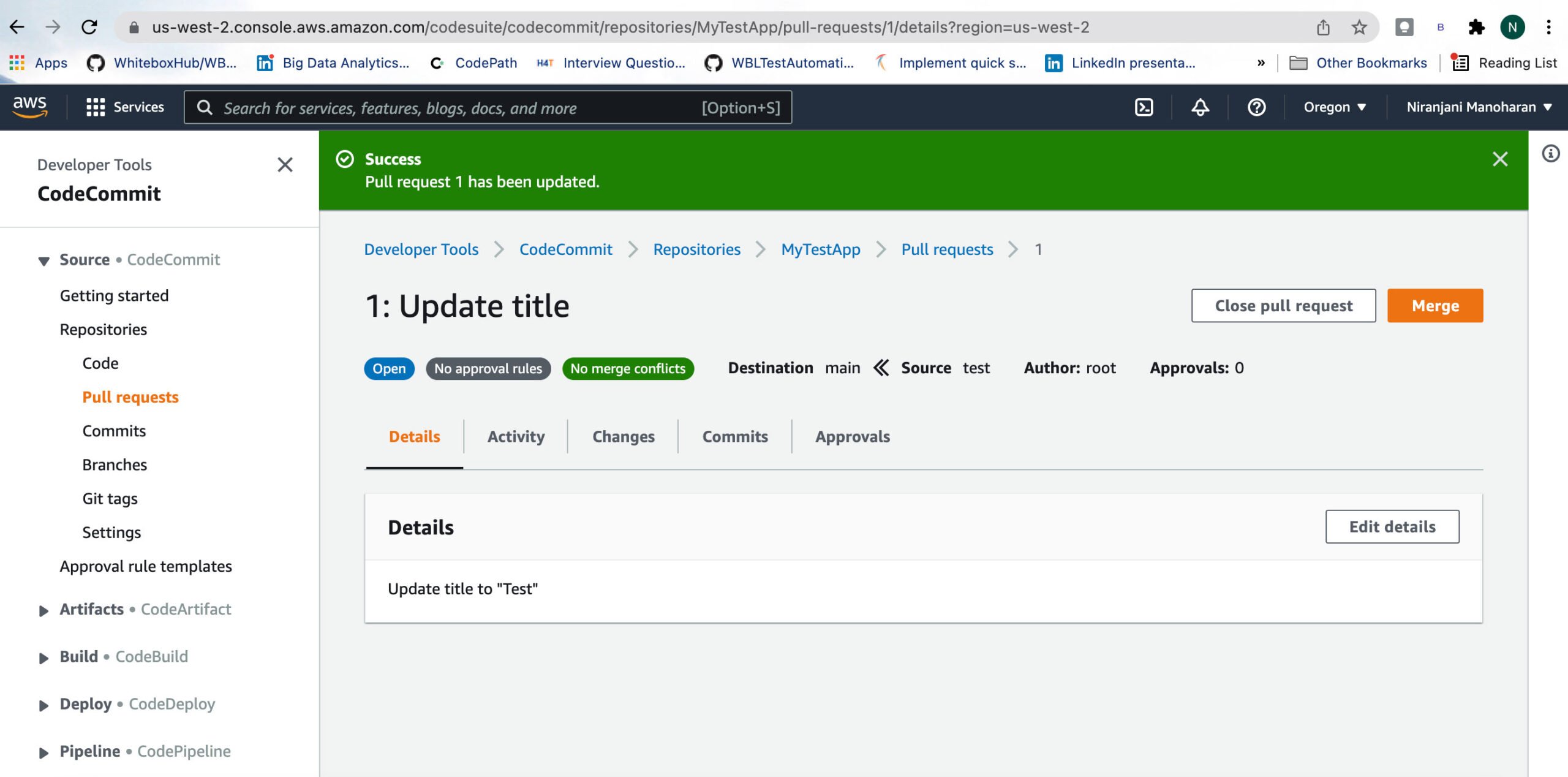
This image shows an example of a pull request prior to merging.
AWS CodeBuild
Has the CI job for running your tests failed without even running the test? After analysis, you see the job got kicked off, but the build never happened as it was waiting in the queue, which was a prerequisite for your tests to run; hence they failed as well. This is a common problem faced while using any CI system that doesn’t have auto-scaling capability.
Integrating CodeBuild into Your Testing Workflow
One common challenge for quality teams is managing builds efficiently. AWS CodeBuild helps by automatically scaling to meet the demands of your build jobs. As a fully managed continuous integration service, it compiles source code, runs tests, and produces software packages ready to deploy. The continuous scaling and concurrent build processing eliminate delays caused by queued builds.
Integrating CodeBuild into your CI/CD pipeline automates testing, ensuring consistency and reliability every time you push code to the repository. This streamlined approach saves time and improves software quality.
Leveraging CodeBuild for Test Automation
CodeBuild offers cost-effective test automation through its pay-as-you-go model. You only pay for the build time used, which is especially helpful for teams running frequent tests. .
CodeBuild seamlessly integrates with other AWS services, such as CodeCommit and CodePipeline, creating a cohesive workflow. This boosts the efficiency of your testing and deployment processes. You can trigger CodeBuild builds when new code enters a CodeCommit repository or automate deployments through CodePipeline after successful builds and tests.
While there are other CI tools like Jenkins, CircleCI, TravisCI, GitHub Actions, etc., the common bottleneck with these tools is their inability to scale their build queues which ends up causing other jobs to wait and eventually timeout.
CodeBuild uses a serverless framework, a software package for YAML and command-line interface(CLI) development, to deploy code to the AWS Lambda function. It starts docker containers to build the code and shuts down as soon as it completes the task.
Orchestrating Tests with CodePipeline
Now that our application code lives in CodeCommit and CodeBuild is running our builds, how do we orchestrate everything? CodePipeline is the conductor of your CI/CD orchestra. It connects CodeCommit, CodeBuild, and other AWS services, creating an automated workflow for building, testing, and deploying your applications. Testing directly in the cloud, preferably within a non-production environment like staging, is considered best practice. This approach closely mimics real-world scenarios, giving you more accurate insights into your application's performance. Experts recommend this method for reliable testing.
CodePipeline lets you visualize and manage each stage of your release process. You can easily monitor build progress, test results, and deployment status from a single dashboard. This centralized view simplifies troubleshooting and keeps your releases on track. For testing AWS infrastructure, tools like LocalStack and Terraform Tests help validate your infrastructure code without provisioning resources in your AWS account. This saves costs and speeds up the testing process, allowing for faster feedback. This entire process, from code commit to testing and deployment, is easily automated within CI/CD pipelines using tools like CodePipeline, ensuring continuous testing and reliable releases. This integration ensures consistent and reproducible test results, isolated from live AWS resources.
One of the key attributes of CodeBuild that sets it apart from its competitors is its capability to scale its infrastructure and ensure that the customer only pays for the exact time it used to build the application.
CodeBuild is built on top of Azure pipelines and has the capabilities to run specific build commands or add a buildspec.yml file with phases defining each step.
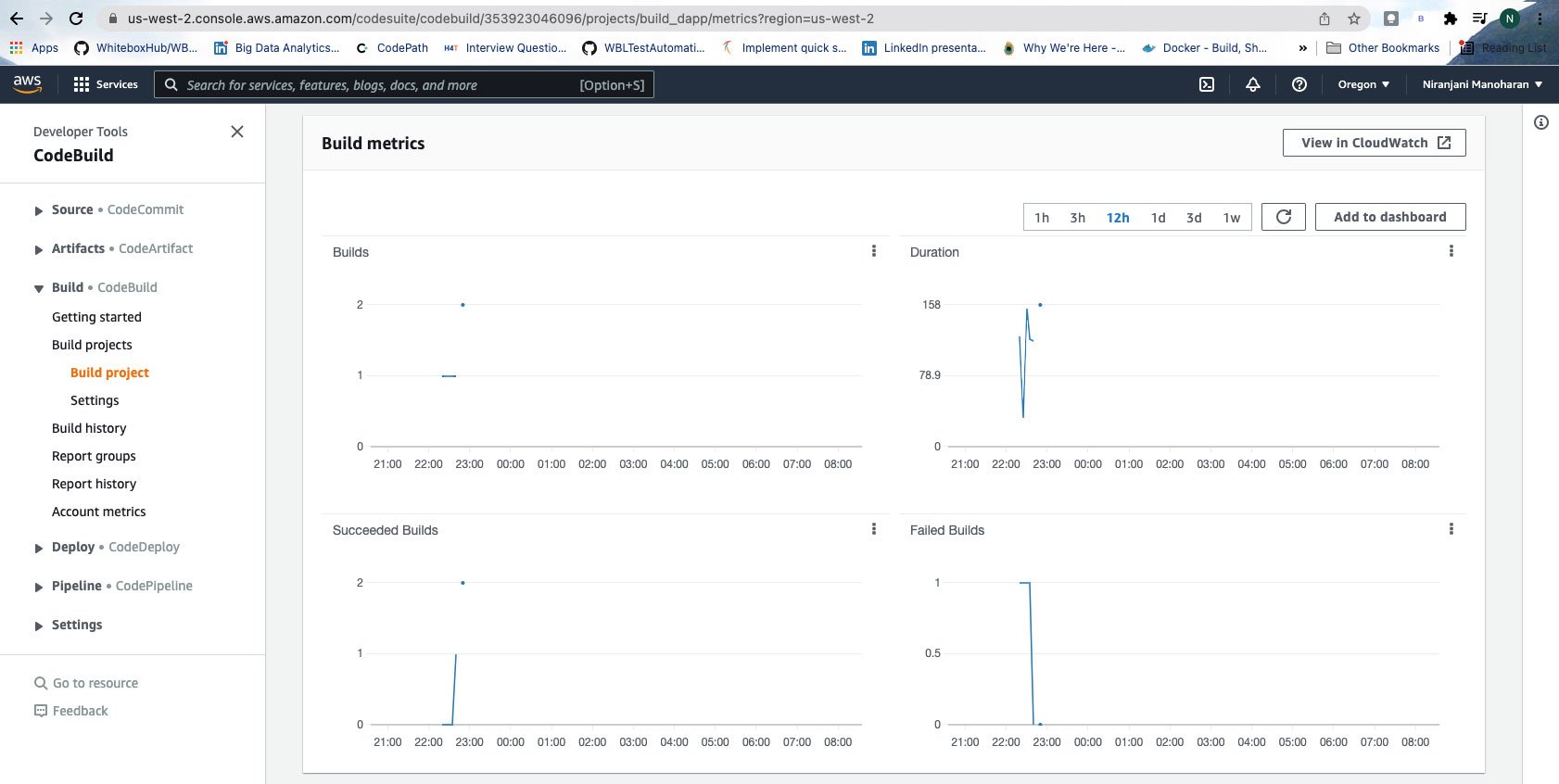
CodeBuild also generates build metrics to give you a comprehensive view of the state of affairs at any given point in time. It is integrated with CloudWatch, so you can view logs and debug issues seamlessly.

AWS CodePipeline
CodePipeline is the capability to automate the build, test, and deploy steps in the CI/CD pipeline. There’s an option to include manual approvals if needed as well. Each of these steps can include actions and conditions associated with them. So, if a step fails, the action is to stop the pipeline and notify the user.
AWS CodeDeploy
Have you ever tried testing staging data in a QA environment or vice versa by mistake? Sometimes this action throws an error because each environment has a config file that defines which DB it should be pointing to. Some organizations have unique environments, whereas, in other places, both these environments share the same DB.
CodeDeploy is a mechanism by which you can automate the process of deploying applications to AWS EC2 instances or serverless lambdas. There is a deployment configuration that is responsible for tracking the progress. The application specification file (AppSpec file) is a YAML or JSON file used by CodeDeploy to manage deployment. It provides information to CodeDeploy about which files from your application revision should be installed on the instance during the deployment’s Install event.
AppSpec file consists of hooks, which are scripts that will execute at one of five hooks representing different app lifecycle events.
A CodeDeploy app deployment consists of five phases:
- ApplicationStop,
- BeforeInstall,
- AfterInstall,
- ApplicationStart, and
- ValidateStatus.
At each stage, your AppSpec YAML file will specify scripts for the service to run. Using AWS CodePipeline, we can pass parameters to different environments using environment variables or AWS Lambda variables.
If your organization is already using AWS for hosting its services, then ensuring your testing infrastructure is built on AWS would be the most cost-effective solution. AWS has cost estimators which can quickly calculate your monthly expenses for your CI/CD pipeline. I hope this brief crash course piqued your interest and you’re motivated to explore more about leveraging AWS for your unique scenario and pitch to your organization.
Testing Strategies for AWS Infrastructure
Testing in the Cloud vs. Local Testing
Choosing between testing in the cloud and local testing is a crucial first step. While local testing offers speed and cost savings during development, it doesn't fully replicate the cloud environment. Think of it like practicing your tennis serve indoors – it helps, but it's not the same as playing on the actual court. Testing directly in the cloud, using a non-production environment, is generally the recommended best practice because it closely mirrors real-world conditions.
Benefits of Cloud-Based Testing
Cloud-based testing allows you to uncover infrastructure-specific issues that local testing might miss. It's like test-driving a car – you need to do it on the road, not just in the garage, to understand its true performance. This approach ensures your application is robust and performs as expected in the actual deployment environment. Plus, using a dedicated testing environment in the cloud keeps your tests isolated from your live production resources, preventing accidental disruptions.
Utilizing LocalStack for Development and Testing
LocalStack provides a convenient way to simulate AWS services locally, which can significantly speed up development and initial testing. It's a great tool for quick iterations and catching basic bugs early on. However, remember that LocalStack doesn't perfectly replicate every nuance of AWS. Therefore, always incorporate testing in a cloud environment that closely resembles your production setup to catch those tricky infrastructure-related issues. This hybrid approach, combining the speed of LocalStack with the realism of cloud testing, often provides the best balance. The AWS documentation offers helpful guidance on this.
Infrastructure as Code (IaC) and Testing
Infrastructure as Code (IaC) is a game-changer for managing and provisioning your infrastructure through code, rather than manual processes. This approach not only simplifies infrastructure management but also opens doors for powerful testing strategies. By defining your infrastructure in code, you create a single source of truth, making it easier to manage and track changes.
Terraform for Managing Test Environments
Terraform is a popular IaC tool that allows you to define and manage your entire AWS infrastructure in code. This means you can create and configure test environments programmatically, ensuring consistency between testing and production. This eliminates manual configuration and reduces the risk of discrepancies that can lead to unexpected issues down the line. You can even use Terraform to spin up and tear down test environments on demand, optimizing your cloud spending.
AWS CDK for Infrastructure Testing
The AWS Cloud Development Kit (CDK) takes IaC a step further by letting you define infrastructure using familiar programming languages like TypeScript, JavaScript, or Python. This allows you to leverage your existing development tools and testing frameworks for infrastructure testing, streamlining your workflow and improving code quality. You can write unit tests, integration tests, and even end-to-end tests for your infrastructure code, just like you would for your application code, ensuring that your infrastructure is as robust as your application itself. The AWS Developer Tools Blog provides valuable insights into CDK testing.
AWS Device Farm for App Testing
Testing your applications on real devices is essential for ensuring a seamless user experience. AWS Device Farm simplifies this process by providing a cloud-based service for testing your iOS, Android, and web applications on a wide range of real devices. This eliminates the need to maintain your own device lab, saving you time and resources. You can run automated tests and even perform remote debugging on real devices, ensuring your application works flawlessly across different platforms and screen sizes.
Best Practices for AWS Infrastructure Testing
Automating Your Tests
Automating your infrastructure tests is key for efficient and reliable deployments. Automated tests can be easily integrated into your CI/CD pipeline, ensuring that every change to your infrastructure is thoroughly tested before it reaches production. This helps catch issues early in the development cycle, preventing costly regressions and ensuring faster time to market.
Implementing Comprehensive Test Coverage
Strive for comprehensive test coverage across all layers of your infrastructure. This includes unit tests for individual components, integration tests for interactions between services, and end-to-end tests for the entire system. A well-rounded testing strategy ensures that your infrastructure is robust, resilient, and can handle real-world traffic and usage patterns. Think of it like building a house – you need to test the foundation, the walls, and the roof to make sure the entire structure is sound.
Frequently Asked Questions
Why is testing my AWS infrastructure so important? Testing your AWS infrastructure is crucial for ensuring your applications are reliable, perform well under stress, and remain secure. It allows you to catch potential problems early on, saving you time and money in the long run. A well-tested infrastructure also helps ensure compliance with security standards and best practices. It's like a dress rehearsal before opening night – you want to make sure everything works smoothly before going live.
What's the difference between testing in the cloud and local testing? Local testing tools like LocalStack offer a fast and cost-effective way to test during development. However, they don't fully replicate the cloud environment. Testing directly in a non-production cloud environment is the best way to catch infrastructure-specific issues and ensure your application performs as expected in real-world conditions. It's best to use a combination of both approaches for optimal results.
How can Infrastructure as Code (IaC) help with testing? IaC tools like Terraform and AWS CDK allow you to define and manage your infrastructure through code. This enables you to automate the creation and configuration of test environments, ensuring consistency and reducing manual errors. You can also apply the same software development principles and testing methodologies to your infrastructure code as you do to your application code, leading to more reliable and maintainable infrastructure.
What is CodePipeline and how does it fit into the testing process? CodePipeline orchestrates your entire CI/CD workflow, connecting services like CodeCommit, CodeBuild, and CodeDeploy. It automates the building, testing, and deployment of your applications, providing a centralized view of your release process. This automation ensures consistent testing and helps you release reliable software updates quickly and efficiently.
How can MuukTest help with my AWS infrastructure testing? MuukTest provides AI-powered test automation services that can help you achieve comprehensive test coverage quickly and efficiently. We integrate with your existing CI/CD workflows and specialize in delivering complete test coverage within 90 days, significantly improving your testing effectiveness and reducing the time it takes to get your applications to market.